Next Animation Studio
China using health tracking mobile system to curtail the spread of coronavirus
Apps from Chinese tech giants Alibaba and Tencent will now host a new health code system that uses QR codes to indicate the health status of citizens, according to a report from CNN.
Amoeba Sisters
Human Body Systems Overview (Updated 2024)
Explore 11 human body systems with the Amoeba Sisters in this updated video (2024). This video focuses on general functions for the following systems (and also provides a few structure examples): Circulatory, Digestive, Endocrine,...
Curated Video
Microsoft Project 2021 From Beginners to Advanced - Outline Numbering and WBS Codes
In this video, we will understand the concept of outline numbering and WBS codes. We will explore how to effectively structure and label project tasks using these codes, facilitating better organization and categorization of project...
Curated Video
Modern Web Design with HTML5, CSS3, and JavaScript - Writing HTML Code
This video explains how to write HTML code. This clip is from the chapter "Introduction to Getting Started with Web Design" of the series "Modern Web Design with HTML5, CSS3, and JavaScript".This section provides an introduction to web...
Ancient Lights Media
Atlas of the United States: The Southeastern Region: Virginia
This clip explores the geography, history, and some important cultural features of Virginia.
Curated Video
I WONDER - What Age Was The Oldest Cat In The World?
This video is answering the question of what age was the oldest cat in the world.
Wonderscape
Samuel Morse and the Invention of Morse Code
This video details Samuel Morse’s collaboration with Leonard Gale and Alfred Vail to develop the first one-wire telegraph. Learn how Morse refined his invention with the creation of Morse Code, a system of dots and dashes that...
Brian McLogan
One Simple Tip For Improving Your Grade
Just because you have been a teacher for a while doesn't make you a good one. Every lesson, every class and every year you have to be looking to improve your instruction. This all clicked with me when I learned about setting goals in...
Curated Video
Predictive Analytics with TensorFlow 10.1: Recommendation Systems
Recommendation systems is a subclass of information filtering system that helps predict the "rating" or "preference" based on the rating provided by users of an item. We will also see collaborative filtering and content-based filtering...
Curated Video
Predictive Analytics with TensorFlow 10.2: Factorization Machines for Recommendation Systems
We will look at two examples for developing a more robust recommendation systems using FM. We will also see FM and their applications in the cold-start recommendation problem. • Understand the factorization machines • Look at the cold...
Curated Video
Design a computer system using tree search and reinforcement learning algorithms : Installing and Setting Up OpenAI Gym
From the section: Getting Started With Reinforcement Learning Using OpenAI Gym. In this section, we will introduce the basics of the reinforcement learning problem, and explain how OpenAI gym helps with developing and research solutions...
Curated Video
Use a real-life example of an AI system to discuss some impacts of cyber attacks : Practical Example of Classification Attacks for MNIST Adversarial Challenge
From the section: Security Test Using Adversarial Attack. In this section, you will test any AI system against the latest attacks with the help of simple tools. The aim of this video is to provide practical experience in attacking a...
Zach Star
Make Your Own Luck - Model Success
When you look at the statistics of marriage/divorce, succeeding in business, making it to graduation, and more, sometimes it can feel a little intimidating. You may be thinking that it seems like the odds are against you. But unless you...
Curated Video
Design a computer system using tree search and reinforcement learning algorithms : Running the Blackjack Environment From the OpenAI Gym
From the section: Model-Free Prediction and Control With Monte Carlo (MC). In this section, we will learn one of two improvements on DP – Monte Carlo, a method which does not require a model of the environment. We talk about a new...
Curated Video
Finding Complex Solutions of Quadratic Equations
This video explains how to find complex solutions of quadratic equations using the method of completing the square. It provides step-by-step instructions on isolating variables, finding perfect square trinomials, and using the square...
Curated Video
Python for Network Forensics 3.4: Parsing System Logs
In this video, we will experiment with correlating log entries to events encountered on the system. • Learn about system logs and how to access them • Learn to interact with the Systemd Journal with Python • Continue development by...
Curated Video
Use a real-life example of an AI system to discuss some impacts of cyber attacks : Building an Image Classification Task and Its Peculiarities
From the section: Testing Image Classification. In this section, you will design specific security tests for image recognition systems. Here you will focus on one particular type of AI solution – image classification, and one category of...
Curated Video
Describe the different types of malware that could affect a computer system or network : Backdoors
From the section: Exploring Malware Functionalities. In this section, you learn how the behavior of malware is different in various classes of malware, and such an insight helps you to understand the class of malware while you are...
Curated Video
Use a real-life example of an AI system to discuss some impacts of cyber attacks : Adversarial Attacks and Their Distinctive Features
From the section: Testing Image Classification. In this section, you will design specific security tests for image recognition systems. Here you will focus on one particular type of AI solution – image classification, and one category of...
Curated Video
I WONDER - What Systems Use JAVA?
This video is answering the question of what systems use JAVA.
TED Talks
TED: How to fix the "bugs" in the net-zero code | Lucas Joppa
Lucas Joppa, Microsoft's first chief environmental officer, thinks about climate change through the lens of coding, and he says the world's current net-zero approach simply won't compute. So how do we create a system that actually...
Rachel's English
Real Life - Hiking in CO * Used in Live Stream June 26, 2020 Part 1
Study English conversation and interesting pronunciation, plus vocabulary words in this real English conversation video as I hike a beautiful mountain in Colorado. See how Americans reduce words in natural conversation to improve...
Curated Video
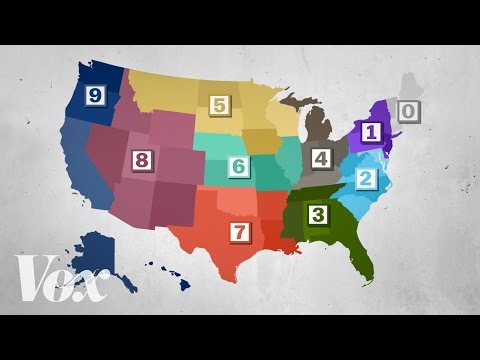
How zip codes helped organize America
Zip codes, explained. Subscribe to our channel! http://goo.gl/0bsAjO Zip codes were invented in 1963 to help the United States Postal Service deal with huge increases in mail volume. The Zone Improvement Plan, or “ZIP” code system of...
Curated Video
The Complete Beginners Guide to Arduino - 2021 - Resistor Color Codes
Resistors are too small to write their values along the side and so use a color code system instead. This lecture will teach you how to read resistor color codes. This clip is from the chapter "Electronic Fundamentals" of the series "The...